Assessment Functions
The Assessment portion of the Dashboard is the mechanism by which an organization conducts and documents their cybersecurity readiness relative to the requirement or practice for each cybersecurity standard. Furthermore, it provides reference materials, best practices, and other guidance to better understand the cybersecurity processes and policies that should be put into place to satisfy the corresponding standard.
The Assessment window, which is a part of the CMMC, 800-171, CSF, and Manufacturing Profile dashboards, supports conducting an assessment and managing your cybersecurity activities using either the NIST Self-Assessment 800-162 Handbook or the NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations publication. The functionality and use of the Assessment is described below.
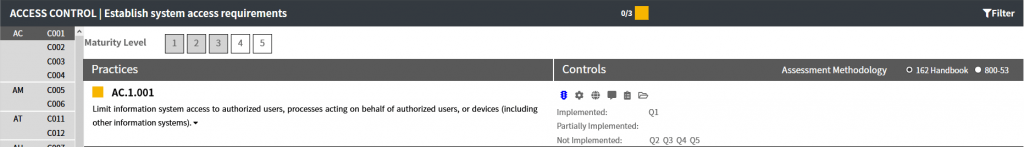
Status
The status page is selected by clicking on the stop light icon. On this page, a status summary is provided. If the selected assessment methodology is the 162 handbook, the status page will show the status of corresponding 162 questions (or a simple question asking if the requirement/practice is implemented when the 162 handbook does not apply). If the 800-53 assessment methodology is selected, the status of each of the relevant 800-53 controls will be display along with the last log entry.

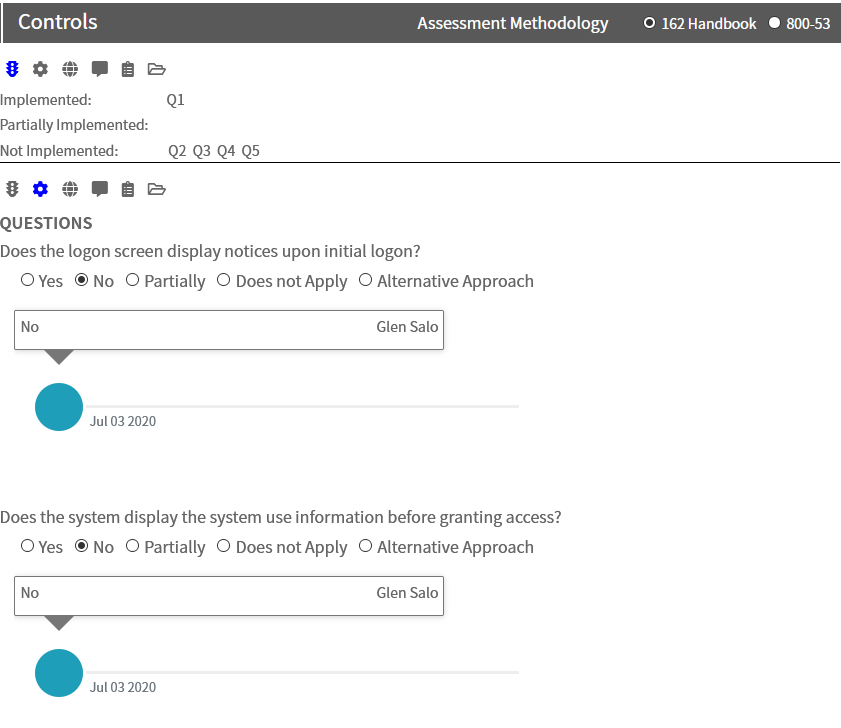
Edit Status
To edit the status, click on the gear icon and update your response to the questions as appropriate.
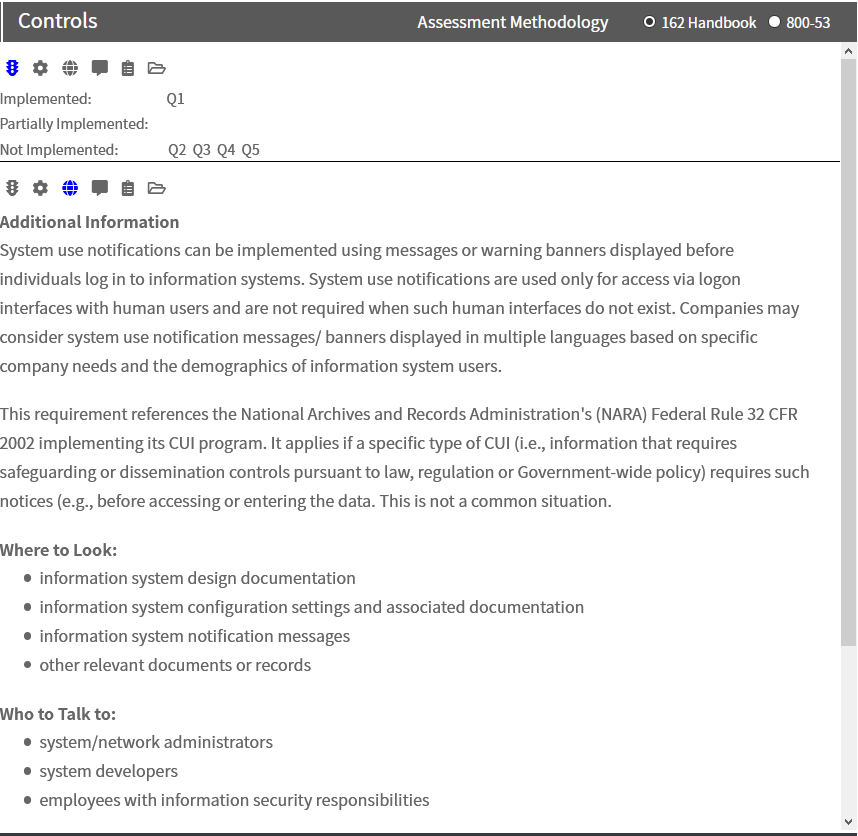
Resources
The resources page (selected by clicking on the globe icon) provides guidance, best practices (800-53 only), and other reference materials to better understand the requirements and suitable solutions.

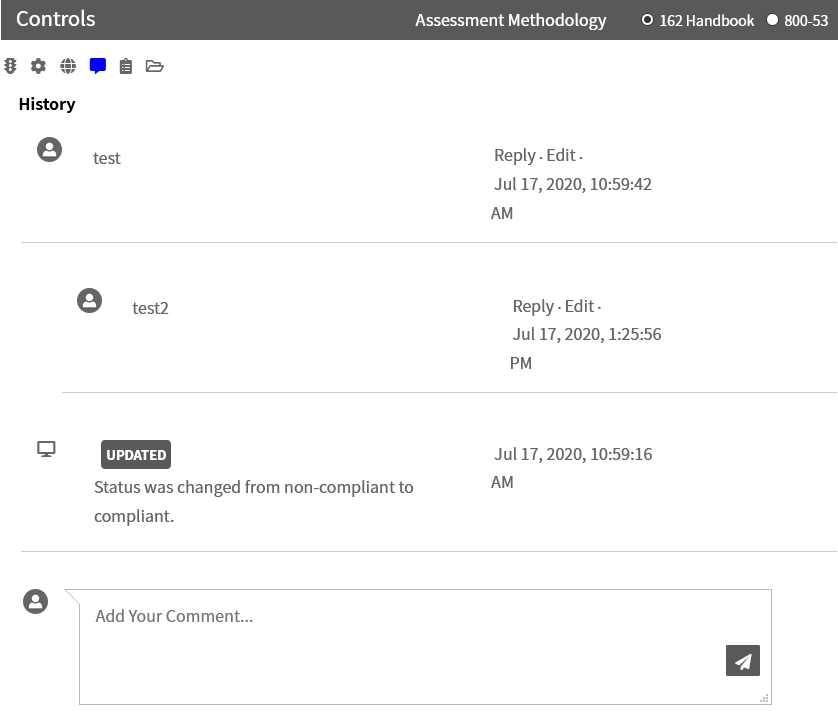
Comments
In addition to providing comments whenever the status is updated, comments, questions, and responses can be posted directly to the comments section for each requirement or practice. The comments function as a blog and can be responded to by others.
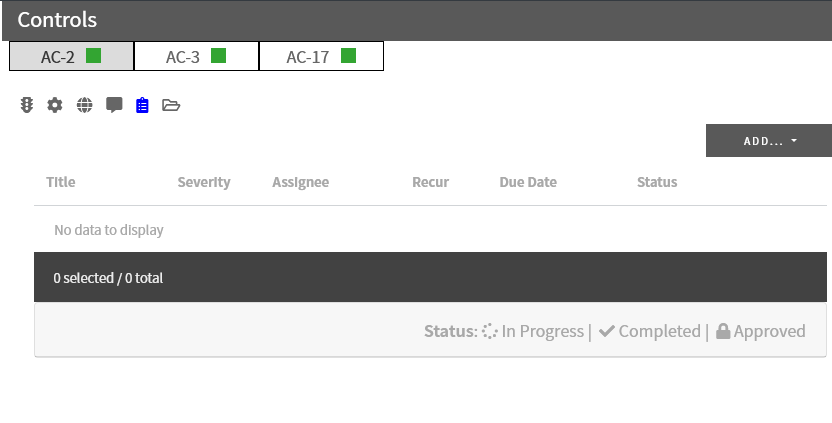
Plan of Action and Milestones (POA&M)
A POA&M is a continuously changing set of tasks that are required to achieve and maintain a desire cybersecurity capability. A description of the POA&M capability function is found here.
The view the tasks associated with a specific requirement or practice, or to create or edit a task, click on the clipboard icon.
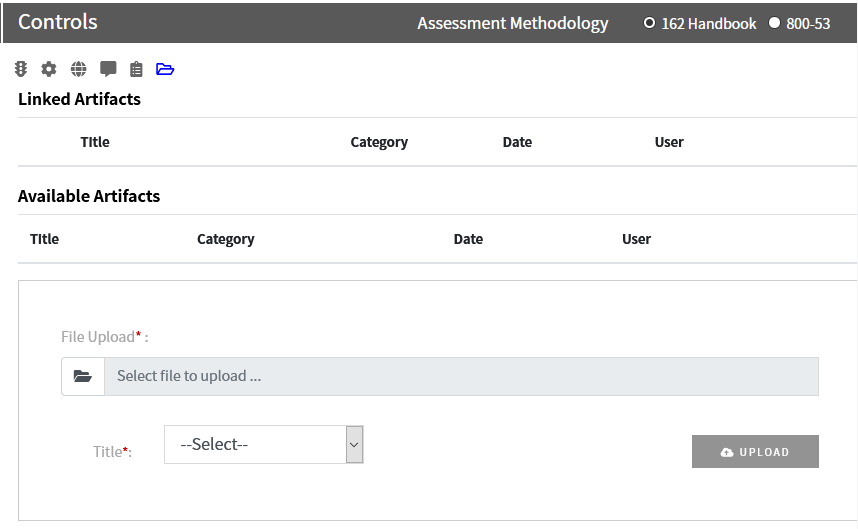
Artifacts
Documents and folders containing documents can be associated with each requirement or practice. To view the associated documents and folders, or to link another document or folder, click on the folder icon.